PowerPoint/IE reload information disclosure vulnerability
Yorick Koster, June 2005
Abstract
This document describes an issue concerning Microsoft PowerPoint when used from within Internet Explorer. It has been discovered that PowerPoint allows an attacker to load an arbitrary HTML page from the Temporery Internet Files folder.
Affected versions
This issue has been tested on a Windows 2000 SP4 system running Internet Explorer 6.0 SP1 with the latest patches applied. The following versions of Office were tested:
* Office 2000
* Office XP
* Office 2003
This issue affects Office 2000 and Office XP SP0. It appears that this issue has been addressed in Office XP SP1.
Fix
This issue was addressed by MS06-010.
Introduction
Internet Explorer allows certain applications to be loaded within the current Internet Explorer window. For example: a user tries to open a Word document. This document will be rendered in a Microsoft Word window that is displayed as part of the Internet Explorer window. Other applications, such as Adobe Reader, also support this behaviour. By doing so, Internet Explorer trusts that this application behaves apropiately.
Because of this, Office documents can be integrated within the current browser session. The user does not have to switch between different application windows. Another interesting thing is the fact that Office applications can render HTML. By setting the Content-Type HTTP header for an HTML page, developers can easily load their HTML page as if it were an Office document. This way, it is possible to 'export' a document as an Excel document without actually creating a 'real' Excel document. This behaviour is demonstrated in the following example:
<?php
header("Content-type: application/vnd.ms-excel");
?>
<html>
<body>
<table><tr>
<td>One</td>
<td>Two</td>
<td>Three</td>
</tr><tr>
<td>1</td>
<td>2</td>
<td>3</td>
</tr></table>
</body>
</html>It appears that Office does not support all HTML tags. For example, Office applications will not execute scripting code between script tags. There is also a difference between various Office applications. For example, PowerPoint does not accept anchor tags with a href value set to javascript:...
PowerPoint reload information disclosure
When a PowerPoint document is loaded in Internet Explorer, it will be displayed in slide show mode. In this mode it is possible to click through the different slides. At the end of the presentation, the user is given the option to reload the presentation. When the presentation is loaded again, the presentation is loaded from the browser cache. Because the presentation is loaded from the cache, the address in the address bar changes to the current user's Temporary Internet Files folder. This behaviour is demonstrated in example 2. The same behaviour is seen when the user uses the scroll bar to scroll down several slides.
A vulnerability has been discovered in the reload mechanism of PowerPoint/Internet Explorer. By setting a special Content-Disposition HTTP header, it is possible to trick Internet Explorer into loading the PowerPoint presentation as an HTML document. Because the reload causes the page to be loaded from the Temporary Internet Files, it is possible to execute arbitrary scripts within the security context of the Temporary Internet Files folder. For a demonstration, see example 3.
<?php
header("Content-type: application/vnd.ms-powerpoint");
header("Content-Disposition: inline; filename=\"hmm\"");
?>
<html>
<body>
</body>
</html>Files in the Temporary Internet Files folder are loaded in the security context of the Internet security zone. Because of this, it is not possible to load any arbitray file from the local computer. Doing so will result in a security exception. It is possible to read every file within the Temporary Internet Folders. Furthermore, the physical location of the Temporary Internet Files can be obtained including the username (assuming a default installation). It is also possible to traverese to the Cookies folder, or to open arbitrary cookies files. However, the Cookies folder is loaded in the restricted sites security zone and consequently it is not possible to obtain the contents of cookies or load arbitray scripting code using a specially crafted cookie (or so it is believed).
A proof of concept has been created that exploits this issue. This proof of concept will load a PowerPoint file. When the user scrolls down, Internet Explorer will reload our PowerPoint document as an HTML document. This causes some JavaScript code to be executed, which will try to read a certain set of files from the Temporary Internet Files folder.
PowerPoint reload information disclosure proof of concept
Steps to reproduce
1. Create an empty PowerPoint presentation
2. Upload the presentation onto a web server
3. Open the presentation in Internet Explorer
4. Click through the presentation until it gives the option to reload the presentation
5. Click to reload, notice that the address bar changes to TIF
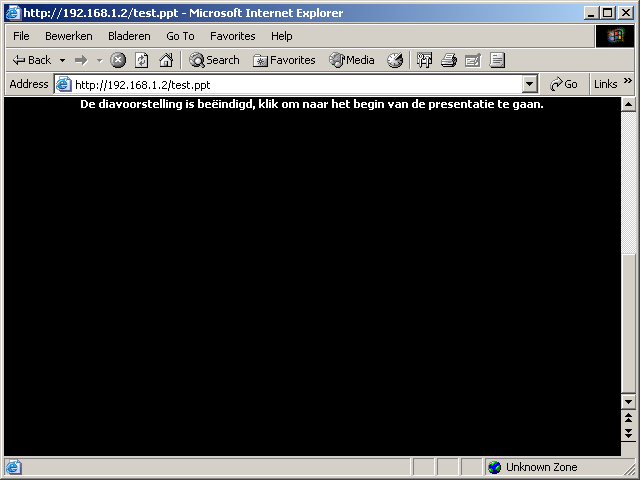
Step 4: click through presentation
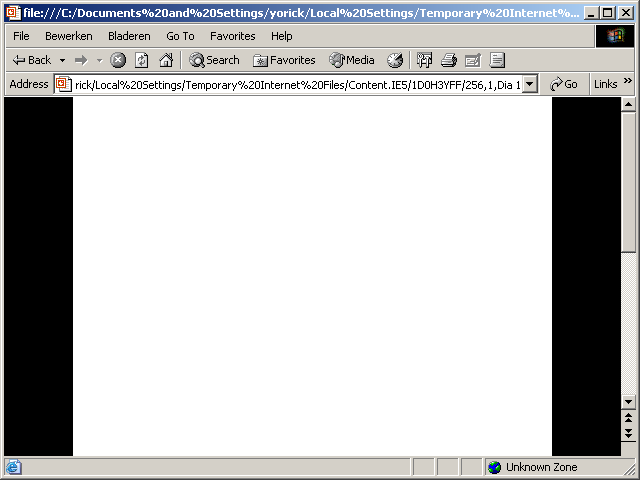
Step 5: reload, watch address bar
Final note
This issue is primarly an Office issue. It issue is triggered by the fact that PowerPoint uses Internet Explorer to reload itself. PowerPoint should be capable in reloading itself using the current PowerPoint instance. It appears that as of Office XP SP1, PowerPoint does exactly this.
Because PowerPoint returns control back to Internet Explorer, Internet Explorer is responsible to determine what type of file it is loading. It seems like Internet Explorer can not properly determine the file type when a Content-Disposition has been set containing a file name without an extension.
It should be noted that when running Office XP or Office 2003, a warning message is displayed when a user tries to open an Office document. However, most user will discard this message, because they are used to open Office documents from within Internet Explorer.
Some limited tests were performed on Windows XP SP2. Windows XP SP2 is also affected by this issue, however the proof of concept that tries to load arbitrary files will fail when a non-existing file is requested. In this case Internet Explorer will display a message box saying that a certain file does not exists. On some systems, the Temporary Internet Files folder may contain temporary files from Outlook Express. These files contain copies of e-mail messages and have predictable file names (wbkXXX.tmp).
